The faster threats are detected (mean time to detection), then the faster they can be responded to (mean time to response). At the end of the day, that’s what Managed Detection and Response (MDR) is all about.
But how do all the components of MDR come together to resolve threats? As alerts are generated from across the environment, where do they go next, and when does the security operation center (SOC) act?
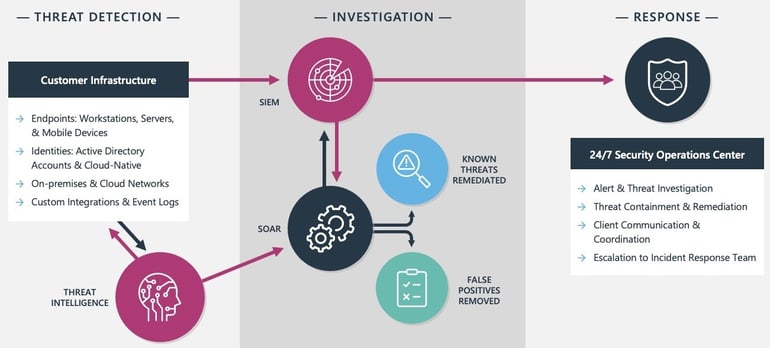
MDR can be broken into three stages: Threat Detection, Investigation, and Response. This blog demonstrates how a security event makes its way through each stage in an MDR program.
The MDR workflow covered below is specific to ProArch’s MDR services. Depending on the MDR provider you work with, the process and tools may be different.
Click here to enlarge image.
Threat Detection
It starts with deploying threat detection solutions that actively collect data and telemetry from various sources within the IT environment to identify potential security threats.
The data comes from across the layers of the environment including endpoints (Endpoint Detection and Response (EDR)), user accounts (Identity Detection and Response (IDR)), cloud, on-premises, and custom integrations (Extended Detection and Response (XDR)). The aggregation of data gives security analysts a more holistic view of the network's activities to address threats promptly.
Threat Investigation
Next, the raw data, including logs, network traffic, and security event information, is collected by the Security Information and Event Management (SIEM) platform. The SIEM serves as the central hub for collecting, analyzing, correlating, and prioritizing security events.
As raw data is ingested into the SIEM, threat intelligence sources enrich the data and add more context around:
- the severity of a known threat
- exploitation likelihood
- potential impact and risk to your environment
This enables critical alerts to be surfaced faster for priority response. Threat intelligence pulls from sources like the dark web, forums, and open-source intelligence to provide early detections of emerging cybersecurity threats, vulnerabilities, and malicious activities.
Now, with the added context, the Security Orchestration, Automation, and Response (SOAR) platform runs automated playbooks to remove false positives, perform additional investigation steps, or perform remediation if the threat is known.
Threat Response
The Security Operations Center is ‘the eyes in the sky’ actively watching every alert from the start. If the threat cannot be resolved through the automated playbooks, they take action.
The data is presented to SOC analysts in a centralized dashboard. They perform threat hunting, containment, and remediation of threats. And work directly with your team to coordinate remediation and escalate to full cybersecurity incident response if necessary.
The detection, investigation, and response processes covered here run every second of every day. The average security operations team receives over 11,000 alerts per day. The importance of automation in cybersecurity can not be emphasized enough. But it’s not easy or inexpensive to find the right tools and people to make this all happen on your own.
That’s where a Managed Detection and Response provider like ProArch can help. Creating an effective in-house threat detection and response program demands substantial expenses, advanced cybersecurity tools, hiring and retaining skilled cybersecurity personnel, and maintaining a 24/7 security operation center (SOC). A lot of things most businesses just don’t have the time or budget to do.
If you have questions on how MDR works, reach out to us anytime. Learn more about how ProArch’s Managed Detection and Response services protect your infrastructure, reputation, and bottom line.


